Preface
This article aims to address the aforementioned issues. Additionally, it endeavours to enhance your understanding of the underlying principles governing the allocation of TCAM resources to ACLs, thereby facilitating the planning of services within your data centre network and mitigating the risk of inadequate TCAM resources.
Introduction to TCAM
|
TCAM Classification
|
Application location
|
|
VFP ACL TCAM.
|
Used for QinQ and other scenarios to control outer VLAN changes.
|
|
IFP ACL TCAM.
|
Inbound ACL: perform access control in the inbound direction.
|
|
EFP ACL TCAM.
|
Outbound ACL: perform access control in the outbound direction.
|
Single Slice (single width) and Double Slice (double width)
|
Matching Domains
|
Illustration
|
Space occupied (bits)
|
|
Vid
|
Resources required for application on SVI interface or Layer 3 sub-interface
|
16
|
|
Etype
|
Matching message-type resources
|
16
|
|
Protocol
|
Resources matching IP protocol numbers
|
8
|
|
Port
|
Resources matching ports
|
8
|
|
PortGroup
|
Port reuse resources
|
12
|
|
IPv4 Src
|
Source IPv4 Resource
|
32
|
|
IPv4-Dst
|
Destination IPv4 Resource
|
32
|
|
IPv6_Src
|
Source IPv6 Resources
|
64 (prefix length is less than or equal to 64) or 128 (prefix length is greater than 64)
|
|
IPv6 Dst
|
Destination IPv6 Resource
|
|
|
Rangcheck
|
Match resources in the Layer 4 port number range
|
32
|
|
L4_Sport
|
Layer 4 source port
|
16
|
|
L4_Dport
|
Layer 4 destination port
|
16
|
|
TCP_Flag
|
Resources matching TCP Flag
|
8
|
The Etype, Port, and PortGroup matching fields are provided based on the specific requirements of the business application, and the Access Control List (ACL) does not have any visual interface for display purposes.
TCAM Features of Box Switches and Frame Switches
● For box switches, the TCAM resources are classified into three distinct categories: VFP ACL TCAM resources, IFP ACL TCAM resources, and EFP ACL TCAM resources. These resources are allocated independently and are not sharable. Within the IFP ACL TCAM resources of box switches, slices are categorized into two types based on their usage: ordinary slices and reserved slices. Ordinary slices can be combined into double slices by pairing two adjacent slices (starting with even-numbered slices) to accommodate services requiring longer matching domains. In contrast, reserved slices do not support splicing; they can only operate in single-slice mode and are designated for specific services or services planned under certain TCAM configurations. Services utilizing reserved slices are restricted to a single slice (single width). Typically, the initial N slices are designated as reserved slices, where N represents one-third of the total number of slices (for instance, the IFP ACL of the box switch RG-S6510-48VS8CQ comprises 12 slices, four of which are reserved—namely, Slice0 through Slice3). Currently, VFP ACL TCAM resources and EFP ACL TCAM resources do not include any reserved slices; all available resources in these categories are classified as common slices.
● In the case of modular switches, the TCAM resources are divided into IFP ACL TCAM resources and EFP ACL TCAM resources. The key distinction between modular switches and box switches lies in the shared and allocated nature of the IFP ACL TCAM resources and EFP ACL TCAM resources in modular switches. Modular switches possess two small slices (the first two slices) classified as reserved slices. Unlike box switches, these reserved slices can be combined, thereby supporting both Single Slice (single-width) and Double Slice (double-width) services, albeit with specific usage restrictions. The reserved slices are permitted for use solely with designated services.
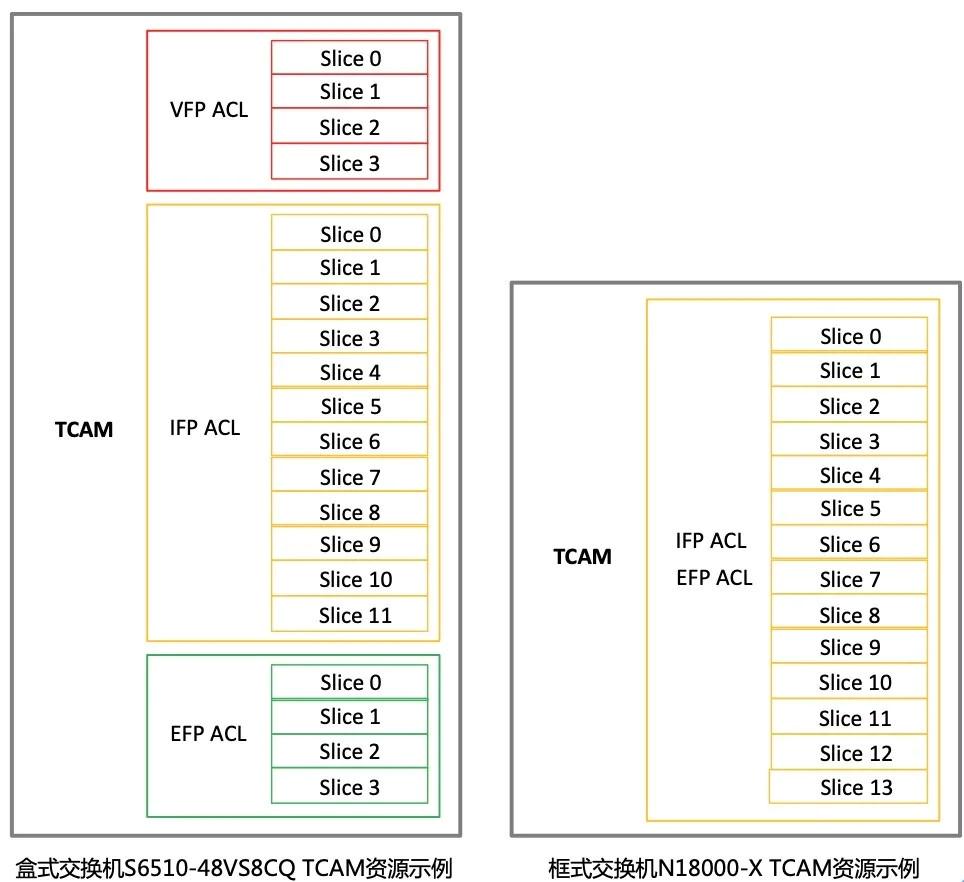
TCAM Resources
|
Common services using TCAM resources
|
The service name displayed on the device
|
|
Use ACL on the interface
|
SECURITY / SECURITY(V6)
|
|
Use ACL globally
|
SECURITY-GBL/SECURITY-GBL(V6)
|
|
Traffic Statistics (Counter-only) Service
|
SECURITY-COUNT/SECURITY-COUNT(V6)
|
|
Policy Routing Service
|
PBR /PBR(V6)
|
|
ERSPAN Business
|
PBM / PBM(V6)
|
|
QOS Service
|
QOS/Q0S(V6)/QOS-CAR/QOS-CAR(V6)
|
|
INT Business
|
INT-INGRESS /INT-INGRESS(V6)
|
|
VXLAN Services
|
VXLAN-CPP/VXLAN-CPP(V6)
|
|
CPP Business
|
CPP/CPP(v6)
|
Different services utilize TCAM resources based on the Slice dimension. While the same service may access the same Slice resource, it is generally the case that most distinct services cannot share the same Slice resource. Consequently, in typical situations, a given Slice can accommodate only one type of service. For instance, if a Slice is already allocated for SECURITY services (where Access Control Lists are employed under the interface), it cannot concurrently store resources for Policy-Based Routing (PBR) services. Therefore, PBR services must be allocated to a separate Slice, even if the Slice designated for SECURITY services has available capacity. Certain services can be integrated in a specific TCAM mode, allowing these integrated services to occupy the same Slice resources; however, this arrangement is subject to specific priority restrictions.
For the CPP service, the aforementioned services will only utilize TCAM resources after the service has been configured. The CPP service is designed to protect the device's CPU through a standard Quality of Service (QoS) differential service model. It is enabled by default upon device startup and cannot be disabled. As a result, when the device is initiated without any configuration, the CPP service automatically consumes TCAM resources by default.
TCAM Operation and Maintenance Method
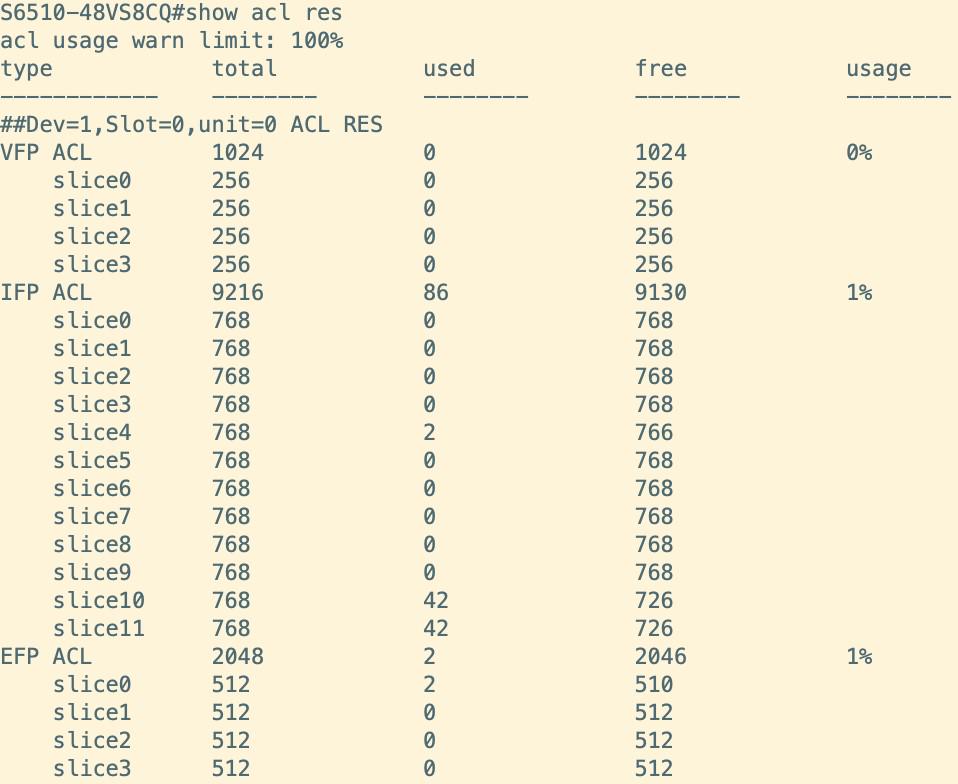
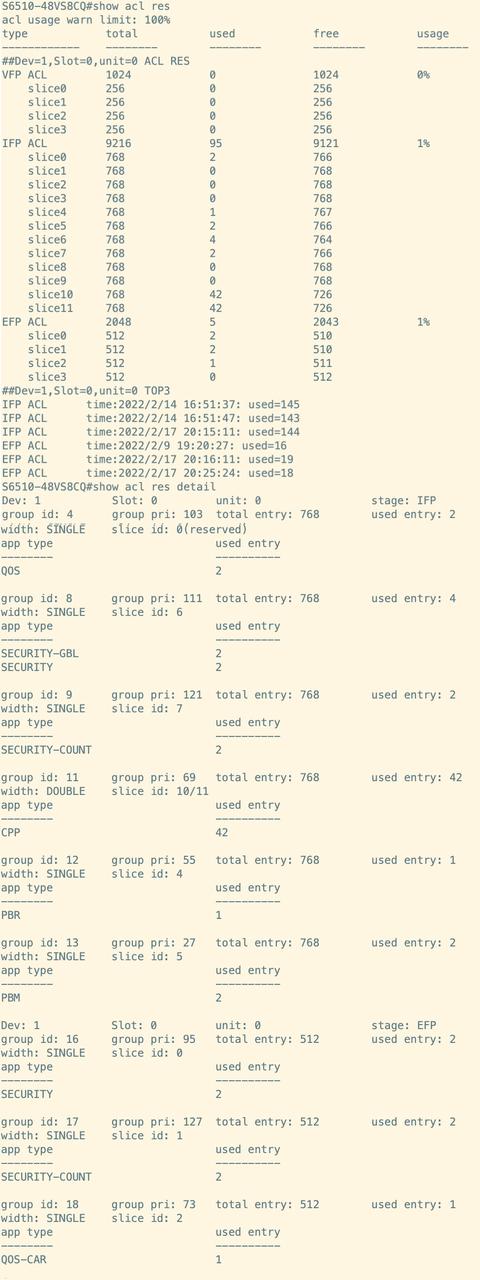
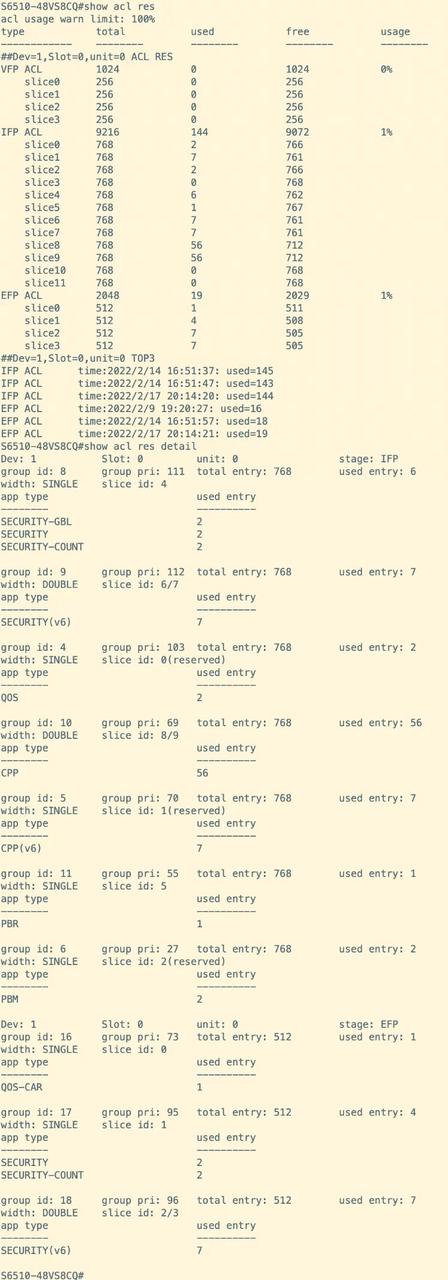
For instance, to assess the TCAM resource utilization of the RG-S6510-48VS8CQ switch, one may execute the "show acl res" command. The output reveals that the VFP ACL TCAM resources comprise four slices (Slice 0 to Slice 3), each with a capacity of 256, resulting in a cumulative total capacity of 1024. The IFP ACL TCAM resources consist of twelve slices (Slice 0 to Slice 11), which are divided into four reserved slices (Slice 0 to Slice 3) and eight common slices (Slice 4 to Slice 11), with each slice possessing a capacity of 768, leading to an overall capacity of 9216. Furthermore, the EFP ACL TCAM resources also consist of four slices (Slice 0 to Slice 3), each with a capacity of 512, culminating in a total capacity of 2048.
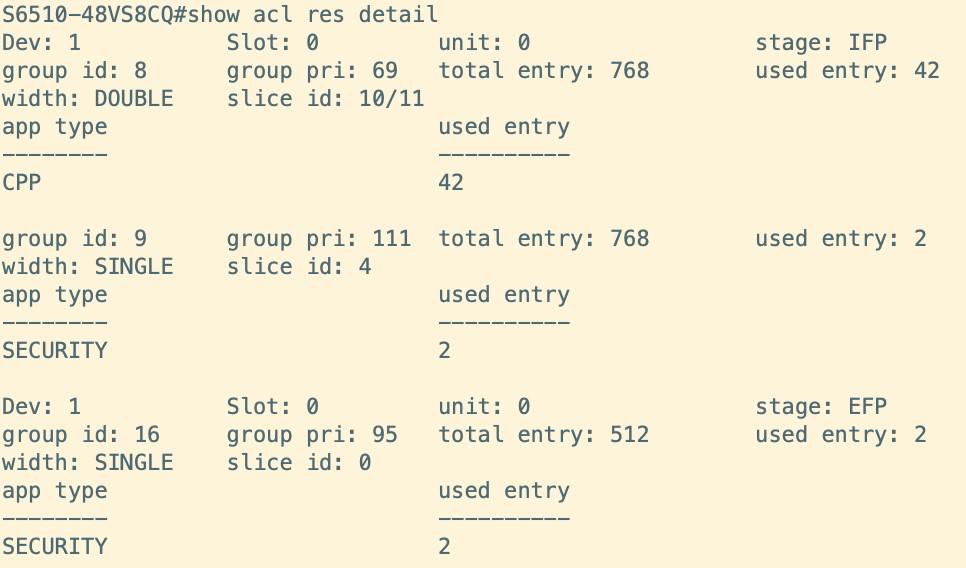
The detailed utilization of TCAM resources for the fixed switch RG-S6510-48VS8CQ can be examined by executing the command "show acl res detail." The acquired information is as follows: Within the IFP ACL TCAM resources, the CPP service occupies a Double Slice resource, utilizing Slices 10 and 11, while the SECURITY service occupies a Single resource, utilizing Slice 4. Regarding the EFP ACL TCAM resources, the SECURITY service occupies a Single resource, utilizing Slice 0.
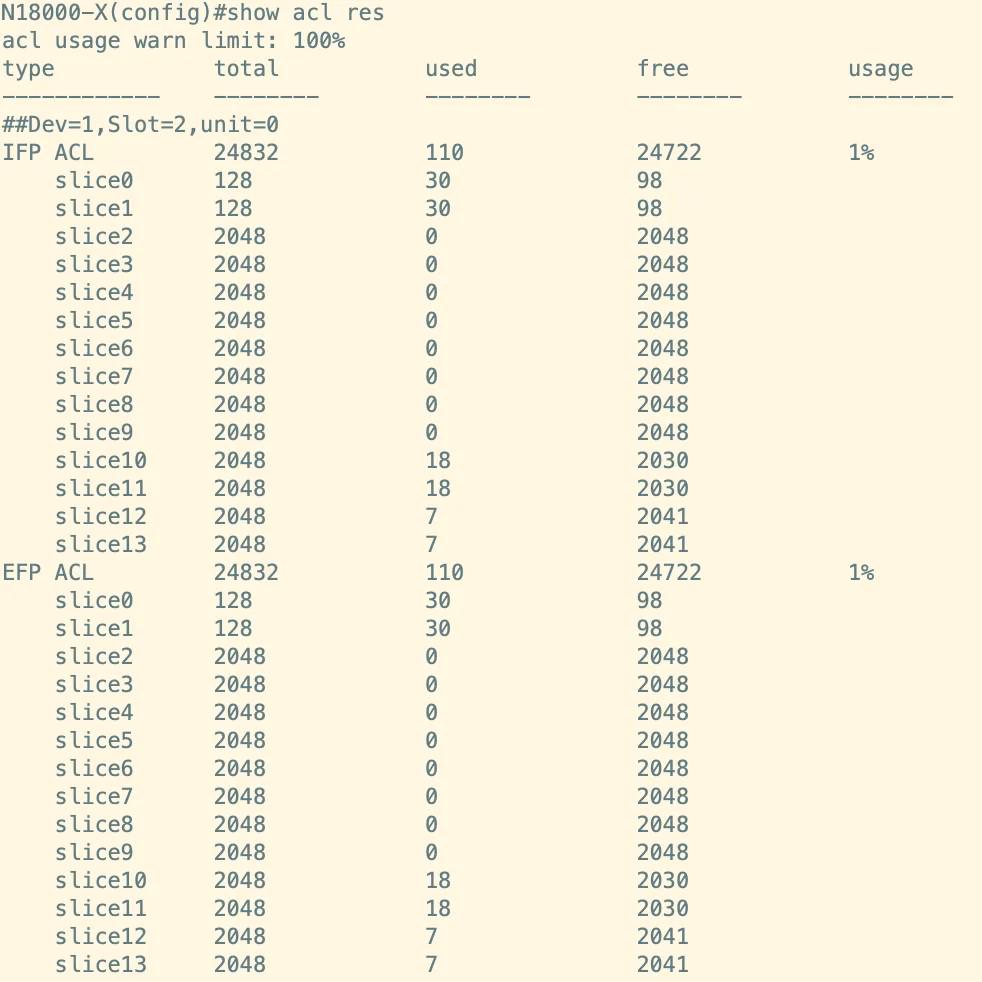
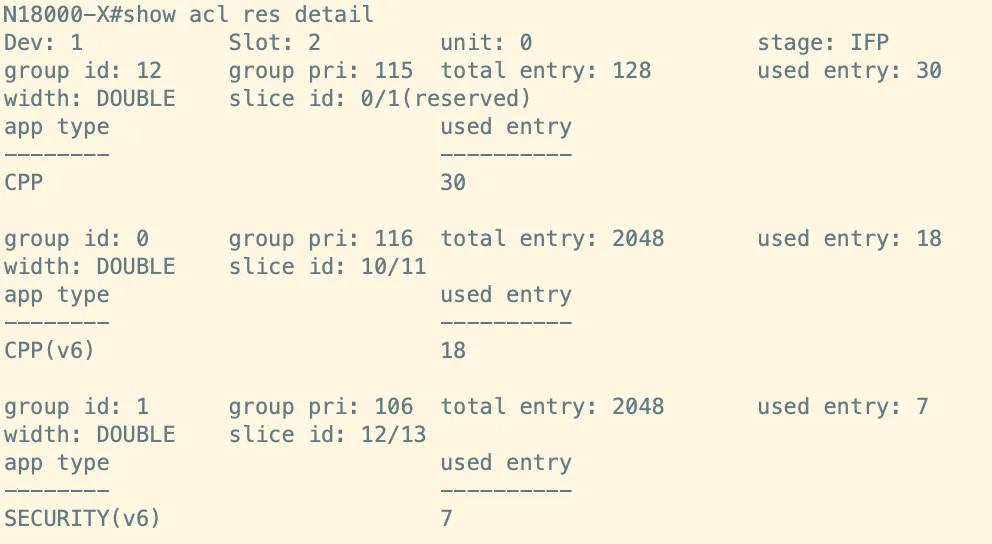
To assess the TCAM status of modular switches designated RG-N18000-X, the "show acl res" command is employed. The information obtained indicates that each board utilizes both IFP ACL and EFP ACL TCAM resources, encompassing a total of 14 slices (Slice 0 through Slice 13). This configuration comprises 2 reserved slices (Slices 0 and 1), each with a total capacity of 128, alongside 12 common slices (Slices 2 through 13), each possessing a total capacity of 2048, resulting in an overall capacity of 24832.
The specific usage of TCAM resources for the modular switch RG-N18000-X can likewise be reviewed by issuing the command "show acl res detail." In this instance, the CPP service occupies one Double Slice resource, utilizing the reserved slice spaces of Slices 0 and 1. Furthermore, the CPP (IPv6) service occupies one Double Slice resource, employing Slices 10 and 11, and the SECURITY (IPv6) service utilizes another Double Slice resource, making use of Slices 12 and 13.
Concerning viewing and adjusting the TCAM mode of data centre switches
|
TCAM Mode
|
Suitable for use scenarios
|
|
Default mode
|
Suitable for common scenarios with few TCAM service types
|
|
ACL-MAX Mode
|
Suitable for IPv4/IPv6 dual-stack scenarios
|
|
ACL-SLICES-ALL Mode
|
A special mode of ACL-MAX mode, which increases the security ACL capacity based on ACL-MAX mode. Only some models of devices support it.
|
|
VXLAN Mode
|
Suitable for VXLAN scenarios
|
|
VXLAN-HASH Mode
|
Suitable for VXLAN scenarios that support VXLAN hash load balancing Suitable for general scenarios that support VXLAN hash load balancing
|
|
ACL-DEFAULT-VXLAN-HASH Mode
|
Suitable for use scenarios
|
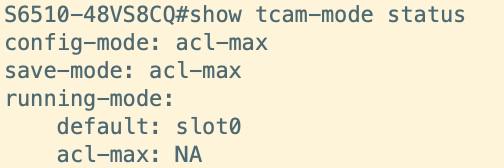
To examine the TCAM working mode of the data centre switch, one may utilize the command "show team-mode status." This command provides insights into the current TCAM mode of the device as well as the TCAM mode that will be in effect following a reboot of the device. Should there be a need to modify the TCAM mode, the command "team-mode acl-max/acl-slices-all/vxlan/vxlan-hash/acl-default-vxlan-hash" can be employed for adjustments. It is important to note that after altering the TCAM mode, it is necessary to save the configuration and perform a complete restart of the device for the changes to take effect.
TCAM Application and Practice
KEY Resource Evaluation: The KEY refers to a processing engine within the device that allocates TCAM resources to services necessitating such resources. Box switches do not require a separate evaluation of KEY resources; an evaluation of Slice resources alone suffices. If Slice resources are adequate, they will also inherently satisfy KEY resource requirements. However, it is essential that switches equipped with DUNE series chips conduct a separate assessment of KEY resources, particularly for those operating on version 12. X.
● Method for Evaluating TCAM Resources in Data Center Switches:
2. Determining Sufficiency of Slices for Business
|
EFP ACL Assessment for Box Switches
|
|
|
Evaluation conditions
|
Evaluation results
|
|
Required for outbound services is less than the number of EFP ACL slices.
|
Slice has sufficient resources.
|
|
The number of EFP ACL slices is less than the number of slices required for outbound services.
|
Adjust TCAM mode or integrate used services
|
|
IFP ACL Evaluation for Box Switches
|
|
|
Evaluation conditions
|
Evaluation results
|
|
The number of slices required for inbound services is less than the number of IFP ACL common slices.
|
Slice has sufficient resources.
|
|
The number of IFP ACL common slices < the number of slices required for inbound services < the total number of IFP ACL slices
|
Configure the deployed services to the actual data centre switch model for verification.
|
|
The total number of IFP ACL slices is less than the number of slices required for inbound services.
|
Adjust TCAM mode or integrate used services.
|
|
Frame switch evaluation
|
|
|
Evaluation conditions
|
Evaluation results
|
|
The total number of slices required for inbound and outbound services is less than the number of IFP/EFPACL common slices.
|
Slice has sufficient resources.
|
|
The number of IFP/EFP ACL common slices < the total number of slices required for inbound and outbound services < the total number of IFP/EFP ACL slices
|
Configure the deployed services to the actual data centre switch model for verification.
|
|
The total number of IFP/EFP ACL slices is less than the total number of slices required for inbound and outbound services.
|
Adjust TCAM mode or integrate the services used.
|
3. Please evaluate whether the KEY resources meet the requirements:
|
The default mode of modular switches
|
|
|
KEY Resource Type
|
KEY Resource Type
|
|
IFP ACL KEY resource
|
7
|
|
EFP ACL KEY resource
|
2
|
|
ACL-MAX Mode for Module Switches
|
|
|
KEY Resource Type
|
KEY Resource Type
|
|
IFP ACL IPv4 KEY resource
|
7
|
|
IFP ACL IPV6 KEY resource
|
7
|
|
EFP ACL KEY resource
|
2
|
4. Case Study on TCAM Resource Insufficiency
Should the issue of insufficient TCAM resources persist after the mode adjustment, the next recommended step is to consolidate the currently employed TCAM services, followed by implementing necessary adjustments or deletions.

Example: Insufficient Slice Resources in RG-S6510-48VS8CQ Switch
|
Business Name
|
Business Configuration
|
Equipment business name
|
TCAM Resource Type
|
|
CPP (IPv4 )
|
CPP
|
IFP
|
|
|
Use ACL on the interface (IP4)
|
ip access-list extended IPV4 ACL IN
|
SECURITY
|
IFP
|
|
10 permit tcp host 1.1.1.1 eq 1111 host 2.2.2.2 eq 2222
|
|||
|
p access-list extended IPy4 ACL OUT
|
|||
|
10 permit tcp host 1.1.1.1 eq 1111 host 2.2.2.2 eq 2222
|
|||
|
interfaceTFGigabitEthernet 0/1
|
AFP
|
||
|
ip access-group IPv4 ACL IN in
|
|||
|
ip access-group IPV4 ACL OUT out
|
|||
|
Traffic Statistics (Counter-only) (IPV4)
|
ip access-list extended COUNT IN
|
SECURITY-COUNT
|
IFP
|
|
10 permit tcp host 1.1.1.1 eq 1111 host 2.2.2.2 eq 2222
|
|||
|
20 permit ip any any
|
|||
|
Ip access list extended COUNT OUT.
|
|||
|
10 permit tcp host 1.1.1.1 eq 1111 host 2.2.2.2 eg 2222
|
|||
|
20 permit ip any any
|
AFP
|
||
|
interface TFGigabitEthernet 0/2
|
|||
|
ip access-group COUNT IN in counter-only
|
|||
|
ip access-group COUNT OUT out counter-only
|
|||
|
Global ACL (IPv4)
|
ip access-list extended GBL IN
|
SECURITY-GBL
|
IFP
|
|
10 permit tcp host 1.1.1.1 eq 1111 host 2.2.2.2 eq 2222
|
|||
|
20 permit ip any any
|
|||
|
ip access-group GBL IN in
|
|||
|
Policy Routing (IPV4)
|
ip access-list extended PBR IPv4
|
PBR
|
IFP
|
|
10 permit tcp host 1.1.1.1 eq 1111 host 2.2.2.2 eq 2222
|
|||
|
route-map PBR IPv4 permit 10
|
|||
|
Match IP address PBR IPv4.
|
|||
|
Set ip next-hop 3.3.3.3
|
|||
|
interface TFGigabitEthernet 0/3
|
|||
|
ip policy route-map PBR IPv4
|
|||
|
QOS (IPV4 )
|
mac access-list extended ARP NO FORWARDING
|
QOS-CAR
|
AFP
|
|
10 permit any arp
|
|||
|
class-maP ARP_NO_FORWARDING
|
|||
|
Match access-grouP ARP NO FORWARDING.
|
|||
|
policy-maP ARP NO FORWARDING
|
|||
|
class ARP NO FORWARDING
|
|||
|
police 00exceed-action drop
|
|||
|
service-policy output ARP NO FORWARDING
|
|||
|
QOS (IPV4 )
|
expert access-list extended RoCEv2-Cnp
|
QOS
|
IFP
|
|
10 permit udp any any any any eq 4791 dscp 35
|
|||
|
Expert access-list extended RoCEv2-Data.
|
|||
|
10 permit udp any any any any eq 4791 dscp af41
|
|||
|
class-map RoCEv2-Data
|
|||
|
match access-group RoCEv2-Data
|
|||
|
class-map RoCEv2-Cnp
|
|||
|
match access-group RoCEv2-Cnp
|
|||
|
policy-map RoCEv2
|
|||
|
class RoCEv2-Data
|
|||
|
Set cos 1 priority
|
|||
|
class RoCEv2-Cnp
|
|||
|
Set cos 2 priority
|
|||
|
service-policy input RoCEv2
|
|||
|
ERSPAN
|
expert access-list extended RDMA
|
PBM
|
IFP
|
|
10 permit udp any any any any eq 4791 udf 1 l5 _head 0 0x8100 0xFF00
|
|||
|
20 permit udp any any any any eq 4791 udf 1 15 head 0 0x1100 0xFF00udf 2 15 head 12 0x6000 0xFF00
|
|||
|
Monitor session 1 span-source
|
|||
|
source interface HundredGigabitEthernet 0/56 rx acI RDMA
|
|||
|
original IP address 1.1.1.1
|
|||
|
destination IP address 2.2.2.2
|
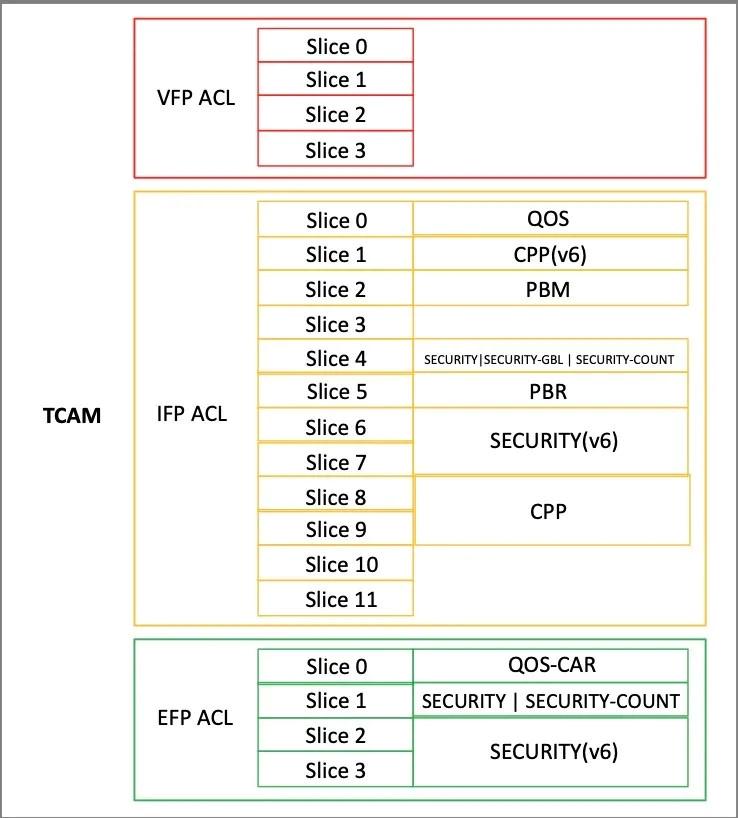
Upon the completion of the service deployment, it is essential to verify the TCAM (Ternary Content Addressable Memory) resource utilization on the device. The accompanying table illustrates that the IFP (Ingress Filter Policy) ACL (Access Control List) TCAM resource consists of 12 slices, which include 4 reserved slices and 8 common slices. Currently, 1 reserved slice and 6 common slices are being utilized. In terms of the EFP (Egress Filter Policy) ACL TCAM resource, there are 4 slices available, of which 3 slices are currently in use.
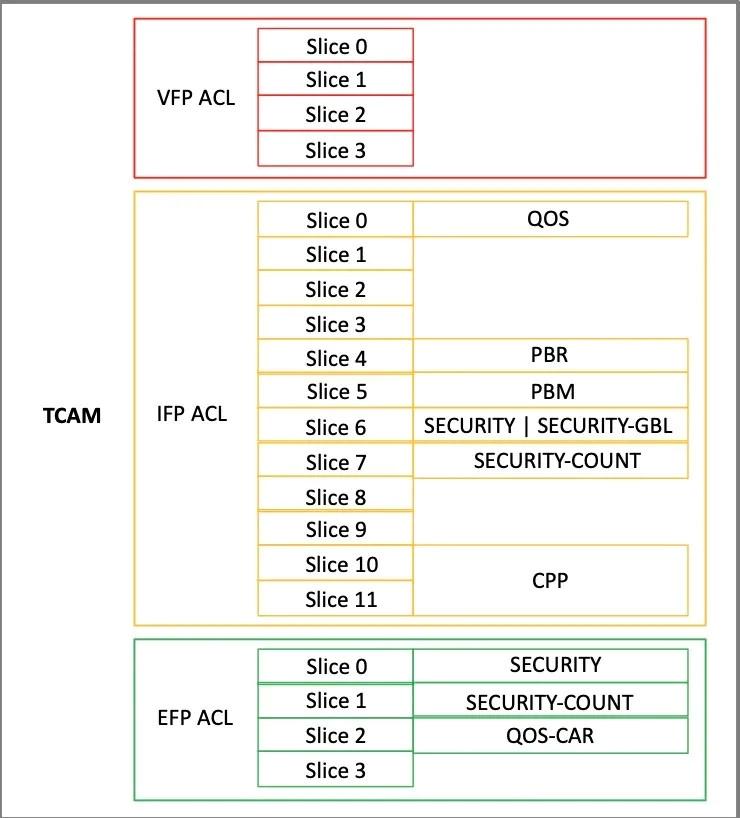
The subsequent figure delineates the specific slice usage by services. For IFP ACL TCAM resources, the QOS (Quality of Service), PBR (Policy-Based Routing), PBM (Policy-Based Management), and SECURITY-COUNT services utilize individual slices, with each consuming one slice. The SECURITY services and SECURITY-GBL services collectively share one slice, utilizing it in total. Additionally, CPP (Class packet processing) services require two slices, as they function as double slices. Regarding the EFP ACL TCAM resources, the SECURITY services, SECURITY-COUNT services, and QOS-CAR services each employ single slices, utilizing one slice each.
In light of the services outlined above, the device is required to activate the IPv6 feature and implement the IPv6 interface ACL function to accommodate specific business requirements. The detailed deployment functions are as follows:
|
Business Name
|
Business Configuration
|
Business Configuration
|
TCAM Resource Type
|
|
Enable IPv6 configuration
|
interface VLAN 100
|
CPP(v6)
|
IFP
|
|
ipv6 enable
|
|||
|
ipv6 address FC01::1/64
|
|||
|
ACL Interface (IPv6)
|
ipv6 access-list IPv6 ACL IN
|
SECURITY(v6)
|
IFP
|
|
10 permit icmp host FC01::1 host FC01::2
|
|||
|
ipv6 access-list IPV6_ACL OUT
|
|||
|
10 permit icmp host FC01::l host FC01::2
|
|||
|
interfaceTFGigabitEthernet 0/1
|
AFP
|
||
|
ipv6 traffic-filter IPv6_ACL_IN in
|
|||
|
ipv6 traffic-filter IPv6_ACL_OUT out
|
Following the activation of the IPv6 functionality, the CPP (v6) service is configured to utilize the Double Slice IFP ACL TCAM resources by default, with an expected reliance on common Slice 8 and Slice 9. Subsequently, upon configuring the IPv6 interface ACL service and invoking the ACL in both the inbound (IN) and outbound (OUT) directions at the interface level, the device is likely to encounter inadequate TCAM resources. At this juncture, it is important to note that three reserved Slice resources remain within the IFP ACL TCAM. As the SECURITY (v6) service is categorized as a Double Slice, it is unable to utilize the reserved Slice resources. Additionally, the EFP ACL TCAM currently has one Slice resource available; however, the SECURITY (v6) service requires two Slice resources due to its Double Slice designation. Consequently, both the IFP ACL TCAM and EFP ACL TCAM will experience insufficient Slice resources.
The device initially operated under an IPv4 single-stack configuration. Upon the activation of the IPv6 functionality and the subsequent deployment of a dual-stack, the issue of insufficient TCAM resources emerged. It is advisable to review the recommended TCAM modes for implementation in the aforementioned scenarios. For an IPv4/IPv6 dual-stack configuration, employing the ACL-MAX mode is strongly recommended. Following the alteration of the device's TCAM mode and a subsequent restart, the device commenced operation in ACL-MAX mode. Upon re-enabling the IPv6 functionality and deploying the IPv6 interface ACL function, there emerged no further TCAM resource constraints. At this point, the TCAM resources of the device should be assessed, as depicted in the accompanying figure. The CPP (v6) service and SECURITY (v6) service are shown to be utilizing TCAM resources effectively.
The accompanying figure illustrates the specifics regarding the slices allocated to the various services. For IFP ACL TCAM resources, the QOS services, CPP (v6) services, PBM services, and PBR services each employ one slice as a single slice. In contrast, the SECURITY services, SECURITY-GBL services, and SECURITY-COUNT services collectively utilize one slice. The SECURITY (v6) services and CPP services, being Double Slices, each require two slices. With respect to EFP ACL TCAM resources, QOS-CAR services are single slices that utilize one slice; SECURITY services and SECURITY-COUNT services again share a single slice for total utilization of one slice; whereas the SECURITY (v6) services necessitate two slices as Double Slices.
In the case of insufficient KEY resources within a modular switch (RG-N18000-X), the following TCAM services are deployed in an IPv4/IPv6 dual-stack scenario:
|
Business Name
|
Business Configuration
|
Equipment business name
|
TCAM Resource Type
|
|
CPP (IPv4)
|
CPP
|
IFP
|
|
|
Enable IPv6
|
interface VLAN 100
|
CPP(v6)
|
IFP
|
|
ipv6 enable
|
|||
|
ipv6 address FC01::1/64
|
|||
|
Global ACL
|
ip access-list extended IPv4_ACL IN
|
SECURITY-GBL
|
IFP
|
|
10 permit tcp host 1.1.1.1 eq 1111 host 2.2.2.2 eq 2222
|
|||
|
20 permit ip any any
|
|||
|
ip access-group IPv4_ACL_IN in
|
|||
|
Global ACL (IPv6)
|
ipv6 access-list IPv6 ACL IN
|
SECURITY-GBL(v6)
|
IFP
|
|
10 permit icmp host FC01::l host FC01::2
|
|||
|
ipv6 traffic-filter IPv6_ACL_IN in
|
Upon the completion of the service deployment, it is essential to assess the utilization of TCAM resources on the device. The findings indicate that the IFP ACL TCAM and EFP ACL TCAM resources share a total of 14 slices, which comprise 2 reserved slices and 12 common slices. At present, 2 reserved slices and 5 common slices are utilized. In addition to the evaluation of slice resources, it is imperative for modular switches to also examine the usage of KEY resources. Currently, there are 7 IFP ACL TCAM KEY resources, with 7 actively in use, and 2 EFP ACL TCAM KEY resources, none of which are currently utilized.
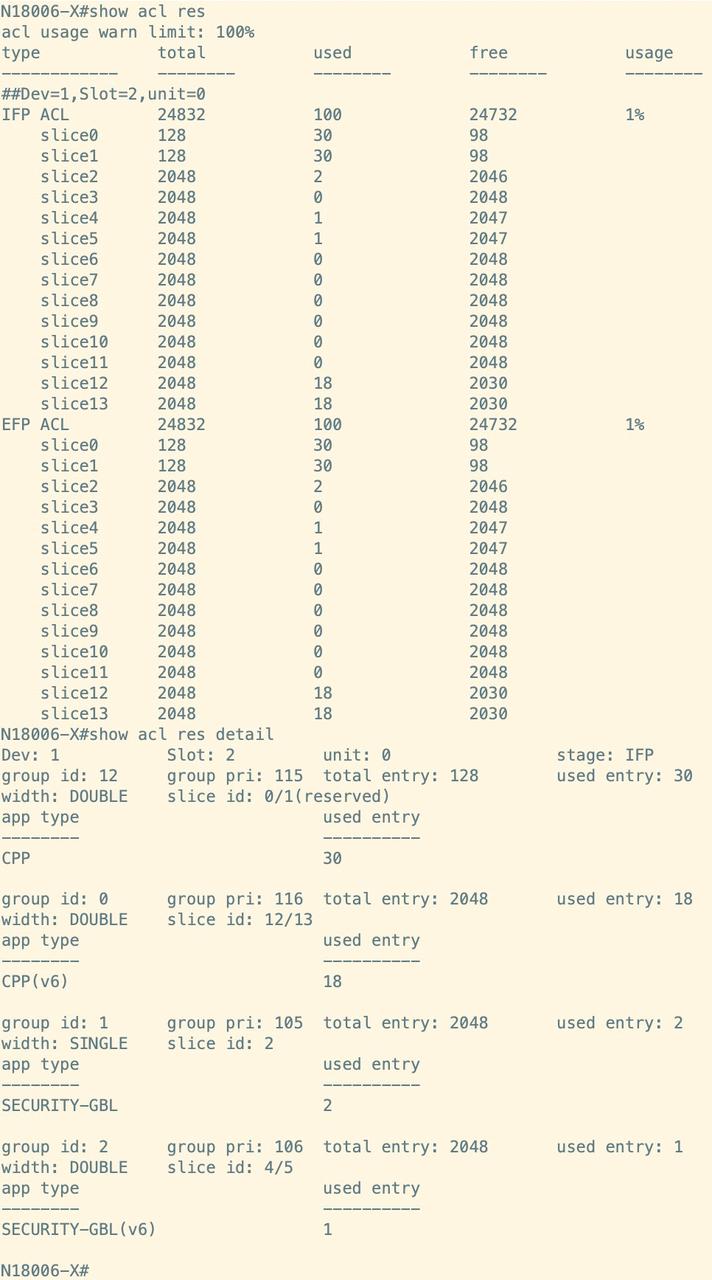
|
The default mode of modular switches
|
|
|
KEY Resource Type
|
KEY Resource Type
|
|
IFP ACL KEY resource
|
7
|
|
EFP ACL KEY resource
|
2
|
Based on the above services, the device adds the IPv4 ERSPAN function. The specific deployment functions are as follows:
|
Business Name
|
Business Configuration
|
Equipment business name
|
Equipment business name
|
|
ERSPAN (IPv4)
|
ip access-list extended ERSPAN IPv4
|
PBM
|
IFP
|
|
10 permit tcp host 1.1.1.1 eq 1111 host 2.2.2.2 eq 2222
|
|||
|
Monitor session 4 span-source
|
|||
|
source interface TenGigabitEthernet 2/1 rx aCI ERSPAN IPV4
|
|||
|
original IP address 1.1.1.1
|
|||
|
destination address 2.2.2.2
|
Upon the completion of the service deployment, it is essential to assess the utilization of TCAM resources on the device. The current findings indicate that the IFP ACL TCAM and EFP ACL TCAM resources collectively share 14 slices, comprised of 2 reserved slices and 12 common slices. At present, 2 reserved slices and 5 common slices are actively in use. In addition to analyzing slice resources, it is also imperative for modular switches to evaluate the allocation of KEY resources. Currently, there are 7 IFP ACL TCAM KEY resources, of which 7 are in active use; further, there are 2 EFP ACL TCAM KEY resources, with none currently in use.
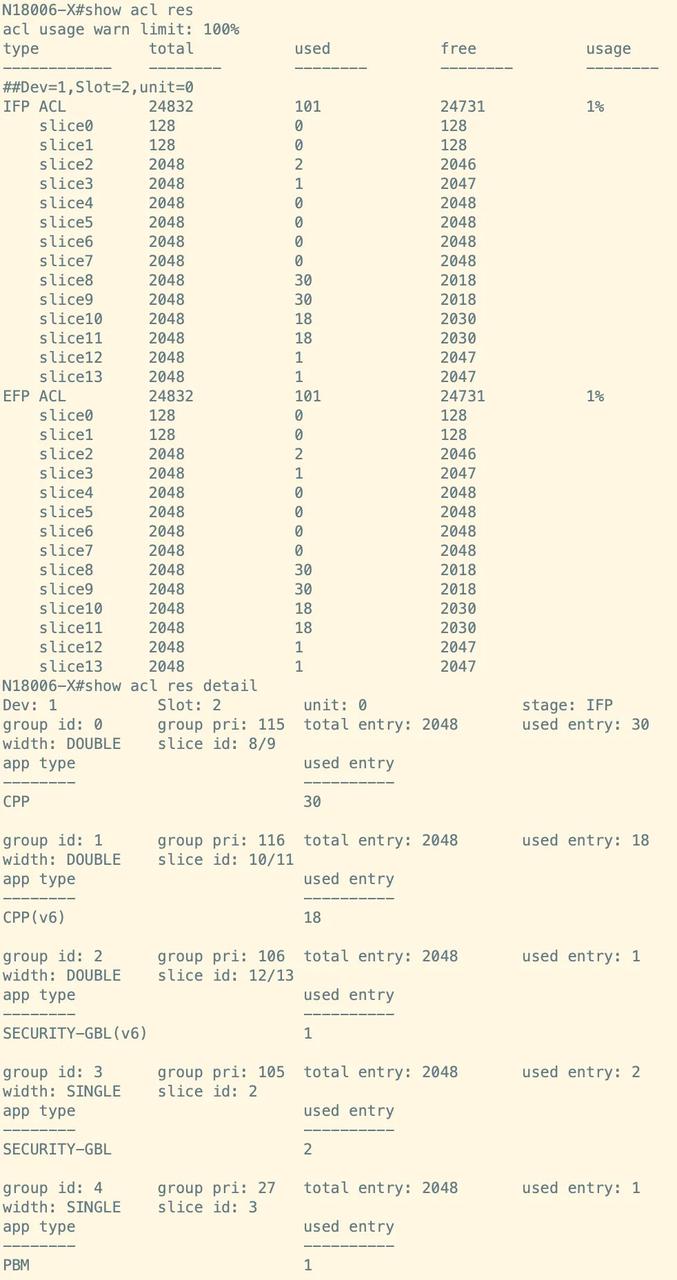
|
ACL-MAX Mode for Module Switches
|
|
|
KEY Resource Type
|
KEY Resource Type
|
|
IFP ACL IPV4 KEY resource
|
7
|
|
IFP ACL IPv6 KEY resource
|
7
|
|
EFP ACL KEY resource
|
2
|
Summary

Related Blogs:
Exploration of Data Center Automated Operation and Maintenance Technology: Zero Configuration of Switches
Technology Feast | How to De-Stack Data Center Network Architecture
Technology Feast | A Brief Discussion on 100G Optical Modules in Data Centers
Research on the Application of Equal Cost Multi-Path (ECMP) Technology in Data Center Networks
Technology Feast | How to build a lossless network for RDMA
Technology Feast | Distributed VXLAN Implementation Solution Based on EVPN
Exploration of Data Center Automated Operation and Maintenance Technology: NETCONF
Technical Feast | A Brief Analysis of MMU Waterline Settings in RDMA Network
Technology Feast | Internet Data Center Network 25G Network Architecture Design
Technology Feast | The "Giant Sword" of Data Center Network Operation and Maintenance
Technology Feast: Routing Protocol Selection for Large Data Centre Networks
Technology Feast | BGP Routing Protocol Planning for Large Data Centres
Technology Feast | Talk about the next generation 25G/100G data centre network
Featured blogs
- CXL 3.0: Solving New Memory Problems in Data Centres (Part 2)
- Ruijie RALB Technology: Revolutionizing Data Center Network Congestion with Advanced Load Balancing
- Multi-Tenant Isolation Technology in AIGC Networks—Data Security and Performance Stability
- Multi-dimensional Comparison and Analysis of AIGC Network Card Dual Uplink Technical Architecture
- A Brief Discussion on the Technical Advantages of the LPO Module in the AIGC Computing Power Network











